
Microsoft が提供する Microsoft 365 のサービス正常性(MO497128)にて、一部のユーザーが [スタート メニュー] や [タスク バー] 内のアプリケーション ショートカットが利用できなくなる SI(サービス インシデント)が発生しています。
“MO497128” のサマリー
- ・[タスク バー] や [スタート メニュー] にあるショートカット アイコンが表示されなくなったり、意図したとおりに動作しない
- ※ 一部ユーザーでは、ショートカット ファイルのパスに依存する実行ファイル(.exe)を実行しようとすると、エラーが発生。
- ※ 詳細については、以下を参照してください。
- https://github.com/microsoft/MDE-PowerBI-Templates/blob/master/ASR_scripts/ASR_rule_Block_Win32_API_calls_from_Office_Macro_issue_Q%26A.md
- ・2023 年 1 月 14 日(土)3:03 AM(2023 年 1 月 13 日 6:03 PM UTC)にセキュリティ インテリジェンス ビルド 1.381.2164.0 の展開が完了し、本アップデートを適用することで新たな事象発生を防ぐことができます。
- ※ Microsoft Defender をビルド 1.381.2164.0 以降にアップデートすることを推奨しています。
- Micosoft Defender アンチ ウイルスの自動アップデートを利用中のユーザーは、セキュリティ インテリジェンスのアップデートを行うために操作する必要はありません。
- Microsoft Defender のアップデートを管理している場合、最新のアップデートを DL(ダウンロード)し、組織内で展開することもできます。
- ※ https://www.microsoft.com/en-us/wdsi/defenderupdates
- ※ この問題については、Microsoft Tech Community のポスト(https://aka.ms/asrfprecovery)にて公開されています。
- ・最近の Windows セキュリティおよび Microsoft Defender for Endpoint サービスのセキュリティ インテリジェンス ビルド(1.381.2134.0、1.381.2140.0、1.381.2152、および 1.381.2163.0)にアップデートした後に、ユーザー デバイスで攻撃面削減(ASR)ルールのリファクタリングを実施し、観測された攻撃者の挙動に適用する範囲を拡大したことで誤検出が連続して発生し、発生。
- これらの検出において、特定の Windows ショートカット(.lnk)ファイルが不正な検出パターンと一致するものと識別され、削除されました。
- ※ アップデート前の攻撃面削減(ASR)ルールではマクロを含む Office ファイルを対象としており、マクロを含む既存ドキュメントを開くことをブロックし、新規作成されたドキュメントのうち、条件に一致するものを削除していました。
- 一方、アップデート後の新しいルールではマクロを含むドキュメントを開くことをブロックしていませんでした。
- ※ この問題は、組織内ユーザーに影響する可能性が高く、Office アプリケーション特有のものではなく、どのアプリケーションのショートカット ファイルにも影響を与える可能性があります。
- ・以下のユーザーには影響がありません。
- ※ ブロック モードで “Office マクロからの Win 32 API 呼び出しをブロックする” ルールをオンにしていないユーザー
- ※ セキュリティ インテリジェンスのビルド(1.381.2134.0, 1.381.2140.0, 1.381.2152, 1.381.2163.0)にアップデートしていないユーザー
目次
Some users are unable to utilize the Application shortcuts on the Start menu and taskbar – MO497128
サービス:Microsoft 365 apps、Microsoft 365 Defender、Microsoft 365 suite
状態:Service restored
ユーザーへの影響:Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
Microsoft 365 のサービス正常性(MO497128)にて、一部のユーザーが [スタート メニュー] や [タスク バー] 内のアプリケーション ショートカットが利用できなくなる SI(サービス インシデント)が発生していました。
本事象の影響を受けている場合、[スタート メニュー] や [タスク バー] 内のアプリケーションのショートカット アイコンが表示されなくなったり、意図したとおりに動作しなくなることがある問題になります。
また、一部ユーザーでは、実行ファイル(.exe)の実行時に、該当ショートカット ファイルのパスに依存している場合、エラーが発生する可能性があります。
詳細については、以下を参照してください。
2023 年 1 月 14 日(土)3:03 AM(2023 年 1 月 13 日 6:03 PM UTC)にセキュリティ インテリジェンス ビルド 1.381.2164.0 の展開が完了しました。
この修正プログラムにより、以前に削除されたショートカット ファイルの復元を行うことはできませんが、新たに誤ってショートカット ファイルの削除が行われることを防ぐことができます。
なお、Microsoft Defender のビルドは、1.381.2164.0 以降にアップデートすることを推奨しています。
- ・Microsoft Defender アンチ ウィルスの自動アップデートを有効にしているユーザーは、セキュリティ インテリジェンスのアップデートを行うために操作する必要はありません。
- ・Microsoft Defender のアップデートを管理している場合、最新のアップデートを DL(ダウンロード)し、組織内に展開することもできます。
- https://www.microsoft.com/en-us/wdsi/defenderupdates
この問題は、2023 年 1 月 14 日(土)3:03 AM(2023 年 1 月 13 日 6:03 PM UTC)に セキュリティ インテリジェンス ビルド 1.381.2164.0 の展開により、本事象を修正しました。
そのため、Microsoft Defender をビルド 1.381.2164.0 以降へアップデートすることを推奨しています。
本事象については、Microsoft Tech Community のポスト(https://aka.ms/asrfprecovery)にて公開される予定です。
なお、この問題は攻撃面削減(ASR)ルールのリファクタリングを実施し、観測された攻撃者の挙動に対する適用範囲を拡大したことにより発生した問題になります。
アップデート前の 攻撃面削減(ASR)ルールではマクロを含む Office ファイルを対象としており、マクロを含む既存ドキュメントを開くことをブロックし、新規作成されたドキュメントのうち、条件に一致するものを削除していました。
一方、アップデート後の新しいルールではマクロを含むドキュメントを開くことをブロックしていませんでした。
この問題は、組織内ユーザーに影響する可能性が高く、Office アプリケーション特有のものではなく、どのアプリケーションのショートカット ファイルにも影響を与える可能性があります。
なお、以下のユーザーには影響がありません。
- ・ブロック モードで “Office マクロからの Win 32 API 呼び出しをブロックする” ルールをオンにしていないユーザー
- ・セキュリティ インテリジェンスのビルド(1.381.2134.0, 1.381.2140.0, 1.381.2152, 1.381.2163.0)にアップデートしていないユーザー
Incident Information
- ・Microsoft Defender Antivirus – Attack Surface Reduction
- ・Microsoft Defender for Endpoint (MDE) – Attack Surface Reduction
User Impact
- Starting on Friday, January 13, 2023, at 8:56 AM UTC, Microsoft Defender customers may have experienced false-positive file deletions.
- These detections occurred where customers had the “Block Win32 API calls from Office Macros” Attack Surface Reduction (ASR) rule enabled in Block mode.
- This rule prevents Visual Basic Application (VBA) Macros from calling Win32 APIs.
- Malware can abuse this capability, such as calling Win32 APIs to launch malicious shellcode without writing anything directly to disk.
- User interaction was not required to experience the file deletions. There are primarily two customer experiences for this incident :
- – Users logging into their devices discovered that shortcut links were missing from the task bar, Windows desktop, the Start Menu, and Microsoft File Explorer pins.
- – Users clicking on shortcuts or the Start Menu observed the shortcuts vanish. As the shortcuts vanished, the programs did not launch.
- These false-positive file deletions impacted the shortcuts and did not delete the programs that they were pointing to.
- Depending on the customer specific environment and the customer experience, not all the deletion actions were logged within the service telemetry.
- In some cases, customers saw dialogs like the example below :
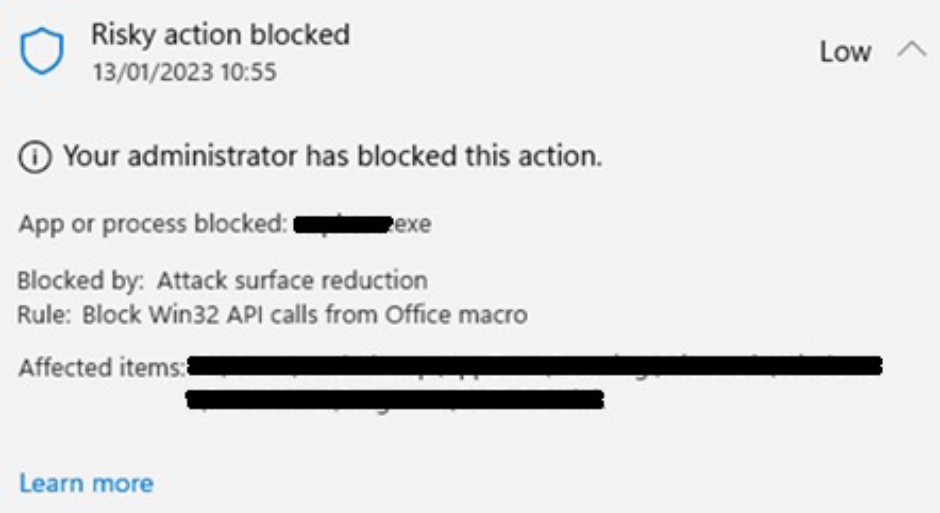
- Microsoft Defender logged some of the file deletion events in a way that was shown through the Microsoft Security Center, Windows system logs, or Microsoft Defender for Endpoint.
Scope of Impact
- Organizations had to have the “Block Win32 API calls from Office Macros” Attack Surface Reduction (ASR) rule enabled in “Block” mode in order for the false-positive detection to occur.
- Organizations who do not leverage the ASR feature or who had this specific rule either “not configured” or in “Audit” mode were not impacted.
- Additionally, only organizations who had updated to security intelligence build(s) 1.381.2134.0, 1.381.2140.0, 1.381.2152, and 1.381.2163.0. were impacted.
- The typical user experience saw multiple files per device impacted.
- The vast majority of the impact was seen in the deletion of .lnk files, but that was not exclusive scoping.
- A full list of affected file types is listed in the table below. The files needed to be loaded into the memory to trigger the detection.
- That condition can be met with customer interaction or part of the background system services.
Incident Start Date and Time
Friday, January 13, 2023, at 8:56 AM UTC
Incident End Date and Time
Thursday, January 19, 2023, at 6:47 AM UTC
Solution
- The false-positive file deletion incident required two categories of solutions in order to identify and restore the files for impacted customers.
- The mitigation section outlines the code-based and service-based solutions that were taken.
- The recovery section outlines what was done to assist customers in recovery of the deleted files.
- Customers are required to complete steps in both sections in order to restore their environments.
Mitigation
Microsoft took multiple steps to mitigate the impact of this incident.
- ・The first step in mitigating impact was the disabling of the Attack Surface Reduction rule from the service side.
- This service change effectively stopped additional file deletion incidents for all customers that have Cloud Protection enabled.
- This change effected the global customer base for this particular ASR rule.
- Customers are able to toggle the rule mode settings in their environment, but enforcement of the rule is not possible until Microsoft restores the rule to production.
- ・The service-side Signature Disable Notification (SDN) was used to mitigate further impact as well.
- Similar to the rule disablement, customers who have Cloud Protections enabled benefit from this notification.
- This feature suppresses detections for the known false-positive incidents.
- Microsoft initially issued a Signature Disable Notification (SDN) at 12:38 PM UTC, on January 13, 2023.
- This first SDN was mistargeted and did not remediate the problem.
- A subsequent SDN was issued at 3:53 PM UTC, that effectively suppressed the false-positive detections.
- ・Microsoft then issued an updated security intelligence build (1.381.2164.0) which removed the root cause logic from the ASR rule.
- This effectively reset the rule logic to the last known good version.
- Customers need to update to security intelligence build 1.381.2164.0 or higher in order to remove the false-positive detection logic.
- Customers utilizing automatic updates for Microsoft Defender antivirus do not need to take additional action to receive the updated security intelligence build.
- Organizations managing updates should download the latest update and deploy it across their environments.
Recovery
- Customers must take additional steps in order to restore their environment(s).
- Microsoft consolidated our official guidance in the Microsoft Defender for Endpoint tech community blog : https://aka.ms/asrfprecovery.
- Recovery options varied based on a customer’s environment and the management tools available.
- The Attack Surface Reduction feature does not have a “roll-back” option, nor does it utilize the recycle bin.
- Microsoft recovery guidance is split into two distinct parts : identifying the impacted inventory and file recovery.
- Identifying the impacted inventory : Microsoft has provided two methods for customers to identify impacted devices in their environment.
- Advanced hunting queries (AHQ) allow E5/A5/P2 customers to search for impacted machines.
- Depending on the size of the customer deployment, modifications are required and documented for the AHQ.
- Customers, including P1/A1/SMB customer SKUs, can use a PowerShell script with similar functionality.
- The scripts and context for each option are provided in the blog.
- File recovery : Microsoft has provided a PowerShell script and executable tool to assist customers in recovering deleted files.
- Instructions on how to run the script and tool via System Center Configuration Manager, Group Policy Object Editor, and Intune are available on the blog.
- These tools assist in restoring the most common functionality impacted by this incident.
- Microsoft has developed several iterations of the tools to address more customer-requested scenarios.
- Customers may use any released version of the tool to assist in recovery, though Microsoft recommends running the latest release.
Root Cause
- The root cause of this false-positive file deletion incident was incorrect detection logic.
- Microsoft was refactoring the ASR rule to expand coverage to observed attacker behavior.
- Previously, this rule targeted Office documents with macros. The rule blocked the opening of existing documents with macros, and deleted newly created documents that matched the criteria.
- The updated rule incorrectly removed the filtering and applied the logic to all inspected files matching the criteria, including the deletion action.
- Q : Why did Microsoft Defender delete the files?
- A : The detection logic incorrectly applied the deletion behavior, which is desired only when files are newly created or downloaded.
- Existing files were previously blocked from executing, but not deleted.
- In this case, the deletion behavior applied to any files that matched the detection logic upon file open.
- This deletion behavior does not utilize file quarantine as it was intended for newly created files only.
- Q : What quality control mechanisms were taken prior to release?
- A : The change was tested locally for effectiveness against the reported attacker behavior and the Office file create case.
- This update was code reviewed by additional security researchers and then run through thousands of automated tests,.
- The automated tests did not cover this case. We released the update through our ringed release framework.
- The ringed releases allow us to release updates to a smaller audience prior to wide availability.
Actions Taken (All times UTC)
Thursday, January 12
- ・11:09 PM – The updated ASR detection code is checked in.
Friday, January 13
- ・6:04 AM – Security Intelligence build 1.381.2140.0 is released publicly to the test in production environment.
- ・8:57 AM – Security Intelligence build 1.381.2140.0 is broadly released across the production environment.
- ・9:05 AM – The first customer reports of an issue with false-positives begin.
- Microsoft support resources started to triage the issue.
- ・10:59 AM – We received the first customer escalations on a possible false-positive outbreak with Microsoft Defender related to ASR rules.
- Users reported that Application shortcuts were not appearing within the Task bar or within the Windows start menu.
- ・11:37 AM – We started to review recent changes to the service and client logs that had been provided by some impacted users.
- ・11:57 AM – We published MO497128 on the Service Health Dashboard (SHD).
- ・12:38 PM – After reviewing ASR rules and recent changes to the Microsoft Defender service, we confirmed that a specific ASR rule
- “Block Win32 API calls from Office macro” was causing impact.
- We issued the first Signature Disable Notification (SDN) to mitigate impact for customers who leverage Cloud protection, however, a flaw in the targeting logic made this initial mitigation ineffective.
- We entered a period of monitoring to determine the effectiveness of the fix, however, after a period of time we confirmed that it was not effective.
- ・2:18 PM – We published recommended actions within the MO497128 post to organizations, that in the short-term, placing the ASR rule into Audit Mode would prevent further impact.
- ・2:33 PM – We reverted the updated ASR rule detection to last known good state.
- We started the process to develop a new Security Intelligence build to deploy the reverted ASR rule.
- We estimated that this could take up to six hours to complete.
- ・3:53 PM – After identifying that the previous SDN did not provide the intended relief due to the flaw in the targeting logic, we issued a second Signature Disable Notification (SDN).
- Customers who leverage cloud protection would have not had any additional impact after this time.
- For customers who did not leverage cloud protection, the deployment of the new build continued to progress.
- ・4:22 PM – We investigated ways to expedite some of the deployment pipeline steps.
- ・5:34 PM – The deployment had progressed through multiple stages of the safe deployment pipeline.
- We continued to expedite the final few stages of the rollout.
- ・6:00 PM – As the build deployment was in the final stages, we started to turn our efforts to recovering impacted shortcut files.
- We started multiple workstreams to investigate both how to identify which files had been affected as well as options on how to recreate the impacted files.
- ・6:48 PM – We completed the deployment of Security Intelligence build 1.381.2164.0.
- This build removed the detection code that was the root cause of the incident.
- Organizations with automatic updates enabled the tool would start to fetch the update the next time the service performed a check for an update.
- Customers would need to update to this new build to prevent additional impact occurring.
- ・7:56 PM – We continued the workstream investigations into the recovery of impacted shortcut files, which included items such as, reviewing command lines within Shadow Copy files and PowerShell scripts creation.
- ・10:08 PM – The main workstreams ongoing were : – Creating manual steps that organizations could use to recover or replace impacted files.
- – Creating a PowerShell script that would parse the Windows Event Log for deleted files and recreate them if possible.
- ・11:46 PM – We continued to make progress in the main workstreams
Saturday, January 14
- ・3:55 AM – After developing a PowerShell script, we started performing testing and validations.
- ・8:12 AM – After testing the script, we released a blog https://aka.ms/asrfprecovery to provide incident information and recovery steps publicly.
- This included the recovery tools v1.0 and manual steps for remediation.
- Additionally, throughout the day we reviewed customer feedback and started making iterations to the scripts and recovery tools to include additional parameters and scenarios.
- ・8:00 PM – After working with impacted organizations with using the recovery tools v1.0 and receiving customer feedback, we started to compile a FAQ section to assist organizations with performing the recovery actions.
Sunday, January 15
- ・2:42 AM – We updated the blog with a FAQ and advanced hunting queries (AHQ) improvements based on customer feedback.
Monday, January 16
- ・6:00 AM – After testing, we released recovery tools v1.1, which included several improvements.
- The blog was updated to reflect the latest information.
- We continued to review customer feedback and make improvements to the recovery tools and guidance provided.
Tuesday, January 17
- ・6:47 AM – The recovery tool v2.0 is released and the blog was updated to reflect the latest.
Wednesday, January 18
- ・7:06 AM – The recovery tool v3.0 is released and the blog was updated to reflect the latest.
Thursday, January 19
- ・2:37 PM – The recovery tool v4.0 is released and the blog was updated to reflect the latest.
Friday, January 20
- ・7:00 PM – We made a decision to close the SHD communication (MO497128) as the majority of the customer impact scenarios had been covered.
- We continued to review customer feedback and make further iterations if needed.
Learnings & Next Steps
January 28, 2023 2:05 AM – Service restored
A post-incident report has been published.
January 25, 2023 10:36 AM – Service restored
A post-incident report has been published.
January 21, 2023 4:48 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users were unable to utilize the Application shortcuts on the Start menu, taskbar, and desktop.
- ・More info : Shortcut icons in the Start menu, taskbar, or desktop may have no longer been visible or may not have worked as intended.
- Additionally, for some users, they may have received errors when trying to run Executable (.exe) files, if they had dependencies on an affected shortcut file path.
- Further information remains published here : https://github.com/microsoft/MDE-PowerBI-Templates/blob/master/ASR_scripts/ASR_rule_Block_Win32_API_calls_from_Office_Macro_issue_Q%26A.md
- We’ve completed an update deployment within the security intelligence build(s) 1.381.2164.0 and later, on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update did not restore previously removed shortcut files, but it did prevent any additional shortcut files from being removed by the incorrect detection logic.
- Customers are encouraged to update Microsoft Defender to build 1.381.2164.0 or later.
- – Customers utilizing automatic updates for Microsoft Defender antivirus do not need to take additional action to receive the updated security intelligence build.
- – Administrators who manage updates directly can download the latest update and deploy it across their environment(s), more information here : https://www.microsoft.com/en-us/wdsi/defenderupdates
- ・Final status : We previously completed an update deployment within the security intelligence build(s) 1.381.2164.0 and later, on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC), which has corrected the behavior.
- Customers are encouraged to update Microsoft Defender to build 1.381.2164.0 or later.
- Further updates regarding this issue will be made available through the Microsoft Tech Community post : https://aka.ms/asrfprecovery.
- ・Scope of impact : This issue may have affected users within your organization; it was not specific to Office apps and could have impacted any application’s shortcut file.
- There was no impact for customers who (1) did not have the “Block Win32 API calls from Office macro” rule turned on in block mode or, (2) did not update to an affected security intelligence build(s) 1.381.2134.0, 1.381.2140.0, 1.381.2152, and 1.381.2163.0.
- ・Start time : Friday, January 13, 2023, 5:56 PM (8:56 AM UTC)
- ・End time : Thursday, January 19, 2023, 3:47 PM (6:47 AM UTC)
- ・Root cause : The root cause of this false-positive file deletion incident was incorrect detection logic.
- Microsoft was refactoring the ASR rule to expand coverage to observed attacker behavior. Previously, this rule targeted Office documents with macros.
- The rule blocked the opening of existing documents with macros, and deleted newly created documents that matched the criteria.
- The updated rule incorrectly removed the filtering and applied the logic to all inspected files matching the criteria, including the deletion action.
- ・Next steps : – For a more comprehensive list of next steps and actions, please refer to the Post Incident Review document.
- We’ll publish a post-incident report within five business days.
January 20, 2023 4:58 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu, taskbar, and desktop.
- ・More info : Shortcut icons in the Start menu, taskbar, or desktop may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on an affected shortcut file path.
- More information has been published here : https://github.com/microsoft/MDE-PowerBI-Templates/blob/master/ASR_scripts/ASR_rule_Block_Win32_API_calls_from_Office_Macro_issue_Q%26A.md
- We’ve completed an update deployment within the security intelligence build(s) 1.381.2164.0 and later, on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being removed by the incorrect detection logic.
- Customers are encouraged to update Microsoft Defender to build 1.381.2164.0 or later.
- These steps have been consolidated into the PowerShell script in the following link to help admins take recovery actions within their environment.
- Users or admins must be a local administrator on the machine that the script will be run on : https://aka.ms/asrfprecovery
- – Customers utilizing automatic updates for Microsoft Defender antivirus do not need to take additional action to receive the updated security intelligence build.
- – Administrators who manage updates directly can download the latest update and deploy it across their environment(s), more information here : https://www.microsoft.com/en-us/wdsi/defenderupdates
- Microsoft has confirmed the effectiveness of steps that administrators and users can take to re-create start menu links for a significant subset of the affected applications that were removed.
- These steps have been consolidated into the PowerShell script in the following link to help admins take recovery actions within their environment.
- Users or admins must be a local administrator on the machine that the script will be run on: https://aka.ms/asrfprecovery
- ・Current status : An additional update has been made to the Microsoft Tech Community post : https://aka.ms/asrfprecovery.
- The blog continues to include the latest version of the script, provides resources for some admins to identify affected machines or files within their environment, and additional steps intended to further aid customers in recovering affected shortcut files.
- ・Scope of impact : This issue may affect users within your organization; it is not specific to Office apps and can impact any application’s shortcut file.
- There is no impact for customers who (1) did not have the “Block Win32 API calls from Office macro” rule turned on in block mode or, (2) did not update to an affected security intelligence build(s) 1.381.2134.0, 1.381.2140.0, 1.381.2152, and 1.381.2163.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to an affected security intelligence build(s) 1.381.2134.0, 1.381.2140.0, 1.381.2152, and 1.381.2163.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Saturday, January 21, 2023, 5:00 AM (1/20/2023, 8:00 PM UTC)
January 19, 2023 4:40 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu, taskbar, and desktop.
- ・More info : Shortcut icons in the Start menu, taskbar, or desktop may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on an affected shortcut file path.
- We’ve completed an update deployment within the security intelligence build(s) 1.381.2164.0 and later, on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being removed by the incorrect detection logic.
- Microsoft has confirmed the effectiveness of steps that administrators and users can take to re-create start menu links for a significant subset of the affected applications that were removed.
- These steps have been consolidated into the PowerShell script in the following link to help admins take recovery actions within their environment.
- Users or admins must be a local administrator on the machine that the script will be run on : https://aka.ms/asrfprecovery
- ・Current status : We’ve posted an update to the Microsoft Tech Community post : https://aka.ms/asrfprecovery, which now includes the latest version of the script intended to further aid customers in recovering affected shortcut files in their environment.
- The resources provided can help admins identify affected machines within their environment, and further steps to run the provided recovery tool/script.
- We’ll continue providing updates as soon as they become available.
- Customers are encouraged to update Microsoft Defender to build 1.381.2164.0 or later.
- Customers utilizing automatic updates for Microsoft Defender antivirus do not need to take additional action to receive the updated security intelligence build.
- Administrators who manage updates directly can download the latest update and deploy it across their environments.
- https://www.microsoft.com/en-us/wdsi/defenderupdates
- ・Scope of impact : This issue may affect users within your organization; it is not specific to Office apps and can impact any application’s shortcut file.
- There is no impact for customers who (1) did not have the “Block Win32 API calls from Office macro” rule turned on in block mode or, (2) did not update to an affected security intelligence build(s) 1.381.2134.0, 1.381.2140.0, 1.381.2152, and 1.381.2163.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to an affected security intelligence build(s) 1.381.2134.0, 1.381.2140.0, 1.381.2152, and 1.381.2163.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Friday, January 20, 2023, 5:00 AM (1/19/2023, 8:00 PM UTC)
January 18, 2023 4:47 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons in the taskbar or Start menu may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- We’ve completed a hotfix deployment within the build 1.381.2164.0 on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- Microsoft has confirmed steps that users can take to recreate start menu links for a significant subset of the affected applications that were deleted. These steps have been consolidated into the PowerShell script in the following link.
- Users must be a local administrator on the machine that the script will be run on : https://aka.ms/asrfprecovery
- ・Current status : We’ve updated the guidance provided within https://aka.ms/asrfprecovery, and have confirmed steps that customers can take to recreate start menu links for a significant sub-set of the affected applications that were removed.
- These have been consolidated into the PowerShell script to help administrators take recovery actions within their environment.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to security intelligence build 1.381.2140.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Wednesday, January 18, 2023, 5:00 AM (1/17/2023, 8:00 PM UTC)
January 16, 2023 4:25 PM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons in the taskbar or Start menu may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- We’ve completed a hotfix deployment within the build 1.381.2164.0 on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- Microsoft has confirmed steps that users can take to recreate start menu links for a significant subset of the affected applications that were deleted. These steps have been consolidated into the PowerShell script in the following link.
- Users must be a local administrator on the machine that the script will be run on : https://aka.ms/asrfprecovery
- ・Current status : We’ve posted an update to https://aka.ms/asrfprecovery as of 7:00 AM UTC, which contains version 1.1 of the script intended to aid customers in recovering affected shortcut files in their environment.
- We expect the updated script to recover additional application types.
- As previously mentioned, we’ve also recently updated https://aka.ms/asrfprecovery to include answers to FAQs.
- We recommend users review the guidance provided while we continue our work to provide more comprehensive solutions.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to security intelligence build 1.381.2140.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Tuesday, January 17, 2023, 5:00 AM (1/16/2023, 8:00 PM UTC)
January 16, 2023 2:50 PM · クイック更新 – Service restored
- We’ve updated https://aka.ms/asrfprecovery to include a Frequently Asked Questions (FAQ) page which may assist affected customers in their recovery efforts.
- This quick update is designed to give the latest information on this issue.
January 16, 2023 4:30 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons in the taskbar or Start menu may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- We’ve completed a hotfix deployment within the build 1.381.2164.0 on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- Microsoft has confirmed steps that users can take to recreate start menu links for a significant subset of the affected applications that were deleted.
- These steps have been consolidated into the PowerShell script in the following link.
Users must be a local administrator on the machine that the script will be run on : https://aka.ms/asrfprecovery - ・Current status : We’ve provided an update to https://aka.ms/asrfprecovery that includes additional details regarding the issue as well as instructions to deploy the script using Microsoft Intune.
- We’re continuing to perform extensive internal tests and are also reviewing customer feedback so we can improve upon the provided workaround details and include additional apps and scenarios.
- We’ll provide updates to https://aka.ms/asrfprecovery as we validate our findings.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to security intelligence build 1.381.2140.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Tuesday, January 17, 2023, 5:00 AM (1/16/2023, 8:00 PM UTC)
January 15, 2023 4:22 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons in the taskbar or Start menu may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- We’ve completed a hotfix deployment within the build 1.381.2164.0 on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- Microsoft has confirmed steps that users can take to recreate start menu links for a significant subset of the affected applications that were deleted.
- These steps have been consolidated into the PowerShell script in the following link.
Users must be a local administrator on the machine that the script will be run on : https://aka.ms/asrfprecovery - ・Current status : We’re performing internal tests on the workaround details provided to aid customers in recovering affected shortcut files in their environment.
- We continue to recommend users follow the steps at https://aka.ms/asrfprecovery and will update the guidance in the site based on our findings.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to security intelligence build 1.381.2140.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Monday, January 16, 2023, 6:00 AM (1/15/2023, 9:00 PM UTC)
January 14, 2023 5:49 PM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons in the taskbar or Start menu may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- We’ve completed a hotfix deployment within the build 1.381.2164.0 on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- Microsoft has confirmed steps that users can take to recreate start menu links for a significant subset of the affected applications that were deleted.
- These steps have been consolidated into the PowerShell script in the following link.
Users must be a local administrator on the machine that the script will be run on : https://aka.ms/asrfprecovery - ・Current status : We’ve successfully optimized the script and tested it in our internal environment.
- We’ve published details of the workaround at https://aka.ms/asrfprecovery.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to security intelligence build 1.381.2140.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Sunday, January 15, 2023, 5:30 AM (1/14/2023, 8:30 PM UTC)
January 14, 2023 4:38 PM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons in the taskbar or Start menu may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- We completed a hotfix deployment within the build 1.381.2164.0 on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- As a temporary work around, affected users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found here : https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- Additionally, if you have not yet received the build containing the fix and if determined appropriate for your environment, admins can put the Attack Surface Reduction (ASR) rule into Audit Mode to avoid further impact.
- Please note that you may need to re-enable the rule once the issue has been fully resolved.
- This can be done through one of the following methods :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- For clarity, note that the offending ASR rule was “Block Win32 API calls from Office macros” with ID: 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b.
- ・Current status : While testing the workaround we discovered that it would not be effective in some customer environments and have been working to optimize it before we make it available.
- We’ll continue working on the potential workaround over the weekend and update when we have more details.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office Apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root Cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to security intelligence build 1.381.2140.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Saturday, January 14, 2023, 9:00 PM (12:00 PM UTC)
January 14, 2023 1:59 PM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons in the taskbar or Start menu may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- We completed a hotfix deployment within the build 1.381.2164.0 on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- As a temporary work around, affected users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found here: https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- Additionally, if you have not yet received the build containing the fix and if determined appropriate for your environment, admins can put the Attack Surface Reduction (ASR) rule into Audit Mode to avoid further impact.
- Please note that you may need to re-enable the rule once the issue has been fully resolved.
- This can be done through one of the following methods :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- For clarity, note that the offending ASR rule was “Block Win32 API calls from Office macros” with ID: 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b.
- ・Current status : We were able to make the potential workaround more robust, but doing so requires us to take a different logistical approach.
- We’re working on extensively validating our workaround and will provide further details in our next update.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office Apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root Cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to security intelligence build 1.381.2140.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Saturday, January 14, 2023, 5:00 PM (8:00 AM UTC)
January 14, 2023 11:02 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons in the taskbar or Start menu may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- We completed a hotfix deployment within the build 1.381.2164.0 on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- As a temporary work around, affected users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found here : https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- Additionally, if you have not yet received the build containing the fix and if determined appropriate for your environment, admins can put the Attack Surface Reduction (ASR) rule into Audit Mode to avoid further impact.
- Please note that you may need to re-enable the rule once the issue has been fully resolved.
- This can be done through one of the following methods :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- For clarity, note that the offending ASR rule was “Block Win32 API calls from Office macros” with ID : 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b.
- ・Current status : We’re finishing up work on a potential workaround that, once complete, should help alleviate impact to some of the affected apps.
- The workaround will be made available in a blog post and we’ll provide more details as we get closer to it going live.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office Apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root Cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to security intelligence build 1.381.2140.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Saturday, January 14, 2023, 4:00 PM (7:00 AM UTC)
January 14, 2023 8:50 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons in the taskbar or Start menu may no longer be visible or may not work as intended.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- We completed a hotfix deployment within the build 1.381.2164.0 on Saturday, January 14, 2023, 3:03 AM (1/13/2023, 6:03 PM UTC).
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- As a temporary work around, affected users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found here : https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- Additionally, if you have not yet received the build containing the fix and if determined appropriate for your environment, admins can put the Attack Surface Reduction (ASR) rule into Audit Mode to avoid further impact.
- Please note that you may need to re-enable the rule once the issue has been fully resolved.
- This can be done through one of the following methods :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- For clarity, note that the offending ASR rule was “Block Win32 API calls from Office macros” with ID : 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b.
- ・Current status : We’ve made significant progress developing potential solutions to address the impact on affected shortcut files and we will provide more information as soon as it becomes available.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office Apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Root Cause : During a recent update to the Windows Security and Microsoft Defender for Endpoint service, user devices experienced a series of false positive detections for the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” after updating to security intelligence build 1.381.2140.0.
- These detections resulted in the identification of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern and were subsequently removed.
- ・Next update by : Saturday, January 14, 2023, 11:00 AM (2:00 AM UTC)
January 14, 2023 6:59 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons may not appear or would not work.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- While we investigate the underlying issue, users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found here : https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- If appropriate, admins can put the Attack Surface Reduction (ASR) rule into Audit Mode to avoid further impact.
- Please note that you may need to re-enable the rule once the issue has been fully resolved.
- This can be done through one of the following methods :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- – For clarity, note that ASR rule “Block Win32 API calls from Office macros” with ID: 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b is the offending rule.
- If determined appropriate for your environment, you can also set the rule to disabled mode.
- Please note, that you may need to manually re-enable the rule once the issue has been full resolved.
- In that case, please use the following Powershell command : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions Disabled
- ・Current status : We’re continuing our investigation into shortcut files that have already been affected by this issue and will provide more information as soon as it becomes available. We completed the hotfix deployment within the build 1.381.2164.0 on Friday, January 13, 2023 at 6:03 PM UTC.
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office Apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Next update by: Saturday, January 14, 2023, 9:00 AM (12:00 AM UTC)
January 14, 2023 5:21 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons may not appear or would not work.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- While we investigate the underlying issue, users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher. More details on the Microsoft 365 app launcher can be found here : https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- If appropriate, admins can put the Attack Surface Reduction (ASR) rule into Audit Mode to avoid further impact.
- Please note that you may need to re-enable the rule once the issue has been fully resolved.
- This can be done through one of the following methods :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- – For clarity, note that ASR rule “Block Win32 API calls from Office macros” with ID : 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b is the offending rule.
- If determined appropriate for your environment, you can also set the rule to disabled mode.
- Please note, that you may need to manually re-enable the rule once the issue has been full resolved.
- In that case, please use the following Powershell command : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions Disabled
- ・Current status : The hotfix has completed its deployment within the build 1.381.2164.0.
- If you have automatic updates enabled the tool will fetch the update at the next time the service performs a check for an update.
- This fix update will not restore previously removed shortcut files, but it will prevent any additional shortcut files from being incorrectly removed. We’re investigating shortcut files that have already been affected by this issue.
- Additional guidance on manual mitigation steps detailed in the “more info” section remain available for customers who have not yet adopted the new build containing the fix.
- ・Scope of impact: This issue likely affects users within your organization and is not specific to Office Apps, and can impact any application’s shortcut file.
- There is no impact for customers who do not have the “Block Win32 API calls from Office macro” rule turned on in block mode or did not update to security intelligence update build 1.381.2140.0.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Next update by : Saturday, January 14, 2023, 7:00 AM (1/13/2023, 10:00 PM UTC)
January 14, 2023 3:58 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons may not appear or would not work.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, if they have dependencies on the shortcut file path.
- While we investigate the underlying issue, users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found here : https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- If appropriate, admins can put the Attack Surface Reduction (ASR) rule into Audit Mode to avoid further impact.
- Please note that you may need to re-enable the rule once the issue has been fully resolved.
- This can be done through one of the following methods :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy: https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- – For clarity, note that ASR rule “Block Win32 API calls from Office macros” with ID : 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b is the offending rule.
- If determined appropriate for your environment, you can also set the rule to disabled mode.
- Please note, that you may need to manually re-enable the rule once the issue has been full resolved.
- In that case, please use the following Powershell command : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions Disabled
- ・Current status : The hotfix is currently progressing through the final stages of the deployment, and we expect this to complete shortly.
- Until the fix deploys, for additional guidance on manual mitigation steps please review the More info section above.
- ・Scope of impact : This issue likely affects users within your organization and is not specific to Office Apps, and can impact any application’s shortcut file.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Next update by : Saturday, January 14, 2023, 5:30 AM (1/13/2023, 8:30 PM UTC)
January 14, 2023 2:24 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons may not appear or would not work.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, as they have dependencies on the shortcut files.
- While we investigate the underlying issue, users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- We recommend that you put the Attack Surface Reduction (ASR) rule to Audit Mode to avoid further impact.
- This can be done through the following options :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- – Note that ASR rule “Block Win32 API calls from Office macros” with ID : 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b
- You can also set the rule to disabled mode.
- In that case, please use the following Powershell command : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions Disabled
- Please note, that you may need to manually re-enable the rule once the issue has been full resolved.
- ・Current status : The hotfix has progressed through multiple stages of our safe deployment procedures and we’re continuing our efforts to expedite the mitigation process.
- While the fix deploys, we recommend that you take action to place the offending ASR rule into Audit Mode to prevent further impact until the update has completed.
- Further information on how to perform this action is provided within the More info section of this communication.
- ・Scope of impact : Impact is specific to some users who are served through the affected infrastructure.
- This issue is not specific to Office Apps, and can impact any application’s shortcut file.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Next update by : Saturday, January 14, 2023, 4:00 AM (1/13/2023, 7:00 PM UTC)
January 14, 2023 1:01 AM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons may not appear or would not work.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, as they have dependencies on the shortcut files.
- While we investigate the underlying issue, users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- We recommend that you put the Attack Surface Reduction (ASR) rule to Audit Mode to avoid further impact.
- This can be done through the following options :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- – Note that ASR rule “Block Win32 API calls from Office macros” with ID : 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b
- You can also set the rule to disabled mode.
- In that case, please use the following Powershell command : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions Disabled
- ・Current status : We’re monitoring the change as it deploys to the affected environment and we continue to review options to expedite the deployment.
- Whilst the fix deploys, we recommend that you take action to place the offending ASR rule into Audit Mode and prevent further impact until the update has completed deployment.
- Further information on how to perform these steps are listed within the More info section of this communication.
- ・Scope of impact : Impact is specific to some users who are served through the affected infrastructure.
- This issue is not specific to Office Apps, and can impact any application’s shortcut file.
- ・Start time : Friday, January 13, 2023, 5:51 PM (8:51 AM UTC)
- ・Next update by : Saturday, January 14, 2023, 2:30 AM (1/13/2023, 5:30 PM UTC)
January 14, 2023 12:22 AM · クイック更新 – Service restored
- We’re reviewing options to expedite the deployment of the change which contains the reverted rule.
- We still recommend that you take actions to place the offending ASR rule into Audit Mode.
- Further information on how to perform these steps can be found within the More info section of the earlier communication.
- This quick update is designed to give the latest information on this issue.
January 13, 2023 11:39 PM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons may not appear or would not work.
- Additionally, for some users, they may receive errors when trying to run Executable (.exe) files, as they have dependencies on the shortcut files.
- While we investigate the underlying issue, users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- We recommend that you put the Attack Surface Reduction (ASR) rule to Audit Mode to avoid further impact.
- This can be done through the following options :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy : https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- – Note that ASR rule “Block Win32 API calls from Office macros” with ID : 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b
- You can also set the rule to disabled mode.
- In that case, please use the following Powershell command : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions Disabled
- ・Current status : We reverted the offending ASR rule, however, this change is propagating throughout the environment and could take several hours to complete.
- We recommend that you take action to place the offending ASR rule into Audit Mode and prevent further impact until the update has completed deployment.
- Further information on how to perform these steps are listed within the More info section of this communication.
- ・Scope of impact : Impact is specific to some users who are served through the affected infrastructure.
- This issue is not specific to Office Apps, and can impact any application’s shortcut file.
- ・Next update by : Saturday, January 14, 2023, 1:00 AM (1/13/2023, 4:00 PM UTC)
January 13, 2023 11:18 PM · クイック更新 – Service restored
- We recommend that you put the ASR rule to Audit Mode to avoid further impact.
- This can be done through the following options :
- – Using Powershell : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions AuditMode
- – Using Intune – https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
- – Using Group Policy – https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#group-policy
- – Note that ASR rule “Block Win32 API calls from Office macros” with ID: 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b
- You can also set the rule to disabled mode.
- In that case, please use the following Powershell command : Add-MpPreference -AttackSurfaceReductionRules_Ids 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b -AttackSurfaceReductionRules_Actions Disabled
- This quick update is designed to give the latest information on this issue.
January 13, 2023 10:28 PM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons may not appear or would not work.
- While we investigate the underlying issue, users can directly launch Office Apps by using the Office App, or through the Microsoft 365 app launcher.
- More details on the Microsoft 365 app launcher can be found https://support.microsoft.com/en-us/office/meet-the-microsoft-365-app-launcher-79f12104-6fed-442f-96a0-eb089a3f476a
- ・Current status : We’ve identified that a specific rule was resulting in impact.
- We’ve disabled the rule and we’re testing to verify that this provides relief.
- ・Scope of impact : Impact is specific to some users who are served through the affected infrastructure.
- ・Next update by : Saturday, January 14, 2023, 12:00 AM (1/13/2023, 3:00 PM UTC)
January 13, 2023 10:06 PM · クイック更新 – Service restored
- We’ve identified that a specific rule was resulting in impact.
- We’ve reverted the rule to prevent further impact whilst we investigate further.
- This quick update is designed to give the latest information on this issue.
January 13, 2023 9:32 PM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons may not appear or would not work.
- We’ve received reports that the Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro” is deleting the application shortcuts.
- ・Current status : We’re investigating recent changes to the Microsoft Defender service to identify the underlying root cause and formulate a mitigation plan.
- ・Scope of impact : Impact is specific to some users who are served through the affected infrastructure.
- ・Next update by : Friday, January 13, 2023, 11:00 PM (2:00 PM UTC)
January 13, 2023 8:57 PM – Service restored
- ・Title : Some users are unable to utilize the Application shortcuts on the Start menu and taskbar
- ・User Impact : Users are unable to utilize the Application shortcuts on the Start menu and taskbar.
- ・More info : The shortcut icons may not appear or would not work.
- ・Current status : We’re reviewing customer report data to determine our next troubleshooting steps.
- ・Scope of impact : Impact is specific to some users who are served through the affected infrastructure.
- ・・Next update by : Friday, January 13, 2023, 10:00 PM (1:00 PM UTC)
Microsoft 365 suite 関連記事一覧
Microsoft 365 suite のメッセージ センター関連情報一覧
- ・
- ・
Microsoft 365 suite サービス正常性 関連記事一覧
- ・【トラブルシューティング】オンプレミス ユーザーが多要素認証(MFA)を利用している場合に Microsoft 365 サービスにアクセスできないことがある問題【MO287933】【復旧済み】
- ・【トラブルシューティング】Outlook On The Web(OWA)にアクセスが行えない場合や Microsoft 365 サービスの一部の機能を利用できない可能性がある SI(サービス インシデント)が発生【MO289250】【サービス復旧】
- ・【トラブルシューティング】Microsoft 365 管理センター内にて Microsoft Teams、E メールのストレージ、グループ アクティビティ レポート等が更新されない問題が発生【MO289071】【復旧済み】
- ・【トラブルシューティング】Microsoft 365 管理センター内にて利用状況のレポートに遅延が発生していた問題【MO290334】【復旧済み】
- ・【トラブルシューティング】一部の管理者が Microsoft 365 Suite 内の Microsoft 365 利用状況レポートにアクセスが行えないことがある問題が発生【MO293125】【復旧済み】
- ・【トラブルシューティング】Microsoft 365 の複数のサービスが利用できない場合がある SI(サービス インシデント)が発生【MO402741】【復旧済み】【PIR】
- ・【トラブルシューティング】複数の Microsoft 365 サービスで問題が発生する可能性のある SI(サービス インシデント)が発生中【MO449914】【PIR】
関連リンク
- ・Recovering from Attack Surface Reduction rule shortcut deletions – Microsoft Community Hub:https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/recovering-from-attack-surface-reduction-rule-shortcut-deletions/ba-p/3716011
- ・Home – Microsoft Community Hub:https://techcommunity.microsoft.com/
- ・Microsoft 365 – サブスクリプションで Office アプリを使用|Microsoft 365:
- ・日本マイクロソフト – Official Home Page:https://www.microsoft.com/ja-jp








